Tenant Isolation - What Is It? Do I Need It? (yes)
Tenant isolation helps to prevent data exfiltration by governing which external tenants can communicate via canvas apps and Power Automate flows.

Author: Jacqui Peck
Date: 9 July 2023
Few people are aware that canvas apps and flow only need to adhere to the Power Platform DLP Policies in the tenant or environment they were created and run. However, apps and flows can be pointed to endpoints in different tenants, so long as the user whose connection is being used has appropriate privileges (and with insider threat, this is often always the case). This is a particularly concerning risk for organisations with high levels and valuable levels of intellectual property or who deal with sensitive data (personal information, financial information, health information, etc).
Furthermore, Microsoft Sentinel and Purview do not have the capability to see these types of communications and therefore go undetected. Microsoft are working on a Sentinel/Purview connector to better monitor Power Platform (in private preview as of June 2023, however this seems to fall short of capturing leaked data and may not apply to whole Power Platform).
Feature: Tenant Isolation
Tenant Isolation allows organisations to govern communication to and from their tenant(s) for Azure-AD based connectors in canvas apps and Power Automate flows. That is, it allows organisation to prevent a user from a different tenant connecting to data within their tenant. Organisations can explicitly allow cross-tenant communication using 'allow lists' that allows for unilateral (inbound or outbound) or bilateral (inbound and outbound) communications.
Disclosure - as per Microsoft's documentation, Tenant Isolation only affect Azure AD-based connections:
Tenant isolation makes it easy for administrators to ensure that these connectors can be harnessed in a safe and secure way within the tenant while minimizing the risk of data exfiltration outside the tenant. Tenant isolation allows admins to effectively govern the movement of tenant data from Azure AD authorized data sources to and from their tenant.
Note that Power Platform tenant isolation is different from Azure AD-wide tenant restriction. It doesn't impact Azure AD-based access outside of Power Platform. Power Platform tenant isolation only works for connectors using Azure AD-based authentication such as Office 365 Outlook or SharePoint.
One-Way (Unilateral) Communications:
'Internal users' represent users/guest users within an organisation's tenant. 'External users' represent users from external tenant. All communications require the external tenant to be added to the allow list
- Inbound: Allows external tenant users to create connections to tenant. Blocks internal users creating connection to external tenant. That is, organisations can receiving connections but cannot make external connection.
- Outbound: Allows internal users to create connections to external tenant. Blocks external tenant users creating connections to tenant. That is, organisations can make outbound connections but not receive inbound connections.
Two-Way (Bilateral) Communications:
Communications in both directions (inbound and outbound) are allowed. That is, organisations can make and receive connections to/from external tenants.
Scenario: Data Exfiltration
User 'Alex' works for 'BusinessX' and wants to take copies of files created in SharePoint and save them to their personal Google Drive as they plan on leaving the business in the future. BusinessX has a tenant-wide DLP policy that has blocked Google Drive connector and any documents send externally via Outlook is monitored and captured via Microsoft Purview & Sentinel (automatic labeling applied to all documents).
Testing the Scenario:
To bypass BusinessX DLP policy follow Alex's steps:
-
Alex needs to signed up for a trial tenant
-
Alex then adds their BusinessX account as a member to the trial tenant and assign a Free Power-Automate license.
-
Alex then creates a flow from a template that uses SharePoint and Google Drive connectors.
-
In the flow, created new connections:
a. SharePoint - create a connection using Alex's BusinessX credentials.
b. Google Drive - create new connections to Google Drive connector using Alex's personal-account credentials linked to the Google Drive. -
Once the connections have been establish, point the SharePoint connector to BusinessX target SharePoint folder to extract files and
-
Point the Google Drive connector to the target folder where the files are to be saved. Trigger the flow and watch data flow out of the tenant!
Test Outcome:
The flow will run automatically and save copies of BusinessX SharePoint files to Alex's personal Google Drive folder thus successfully exfiltrating BusinessX data undetected.
Stop Data Exfiltration Using Tenant Isolation:
By design cross-tenant communication is allowed (that is, tenant isolation feature is off by default) and is useful and necessary for many business scenarios. However, a lot of organisation are looking to ensure data stays inside their tenant. For this reason, Microsoft offers the feature "Tenant Isolation". Tenant Isolation allows organisations to explicitly allow communication between approved tenants controlling inbound and outbound traffic from Power Platform connectors.
Effects of Tenant Isolation on Alex's Flow:
Once BusinessX enabled Tenant Isolation, within moments Alex's flow was blocked with the following error message
Error from token exchange: Sign-in with Azure Active Directory account [email protected] failed, due to a tenant isolation policy for tenant XXXXXX-XXXX-XXXX-a80e-XXXXXXX"
If your use case requires a cross-tenant connection, contact your tenant administrator.
Details:
Connection owner tenant: XXXXXX-XXXX-XXXX-b92z-XXXXXXX,
Connection sign-in tenant: XXXXXX-XXXX-XXXX-a70f-XXXXXXX ,
Connector: SharePointHow to Enable Tenant Isolation:
To enable and make changes Tenant Isolation requires either Tenant Global Administrator or Power Platform Administrator security roles that are assigned via Azure AD.
Enable Tenant Isolation:
This will turn tenant isolation on, blocking all communications with the tenant
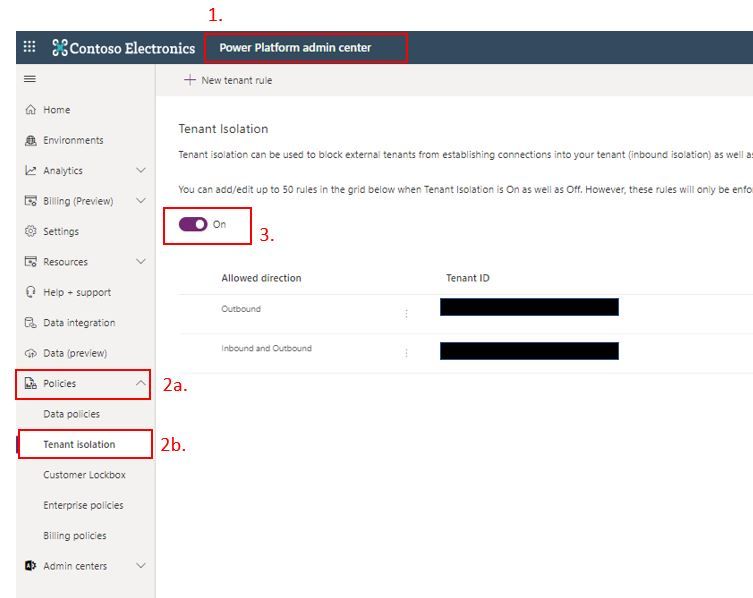
- Sign into the Power Platform Admin Centre
- Select (a) Policies then (b) Tenant isolation
- Toggle to ON position
Allow Lists - Enable Cross-Tenant Communications:
Explicitly allow unilateral or bilateral communications with a specified tenant
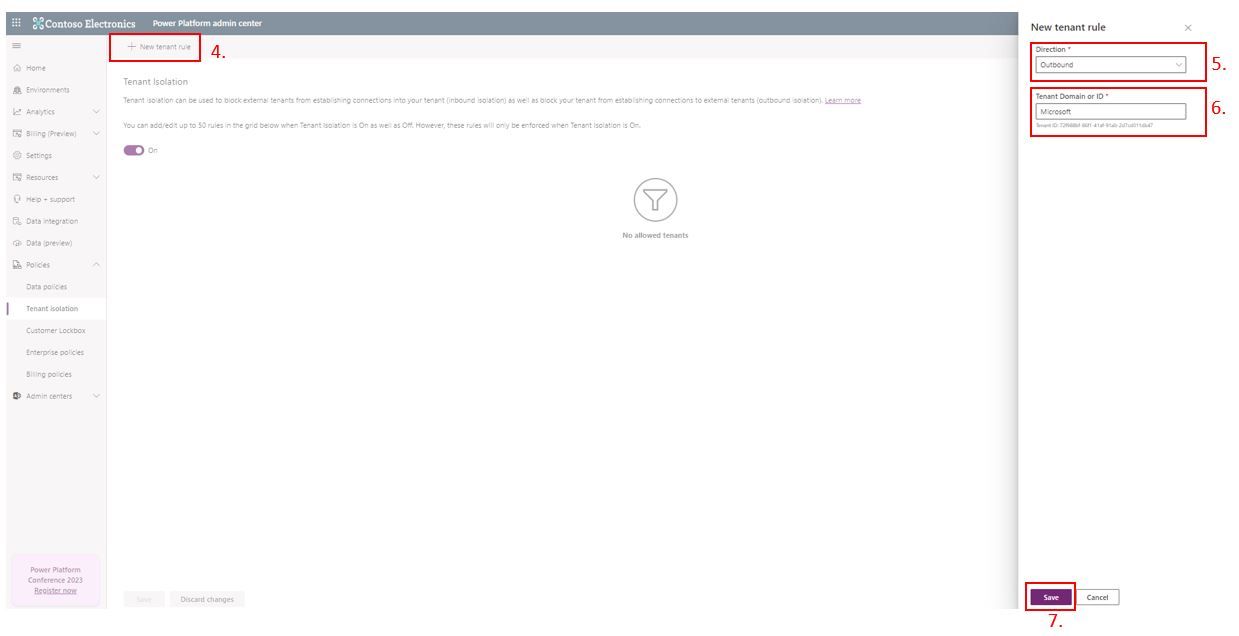
- Select New tenant rule, here a side pane will appear to the right
- Select the direction of communication
- Add the target tenant name or ID (in this example I have used 'Microsoft'). (note: to allow all tenants in a specific direction use “*” )
- Select Save
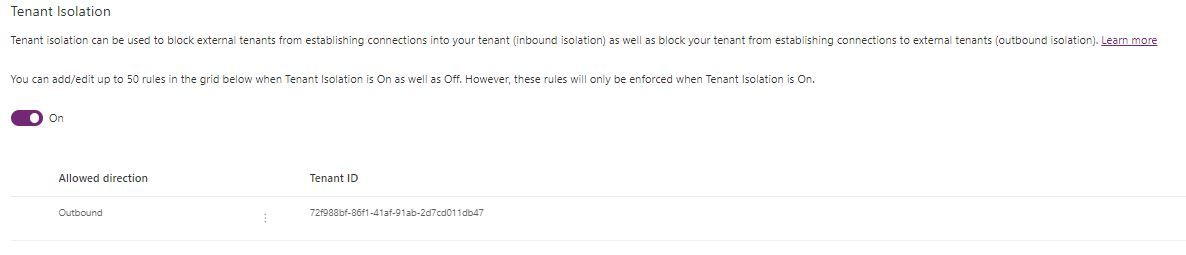
A list of tenant rules will be displayed showing only the tenant ID. All communications not specified in the allow list will be rejected by Power Platform. As only the tenant ID's are shown, it is a good idea to keep a record of this (I would suggest extending the CoE Starter Kit's 'Power Platform Admin View' model-driven app for this).
Impacts and Considerations for Tenant Isolation:
Error messages will appear for users who try to establish new connections using Canvas Apps and Power Automate flows. In my testing, existing connections using Power Automate were impacted immediately with error messages displayed, however, Microsoft does allow up to an hour for tenant isolation to be implemented across all existing connections.
For a list of current see Microsoft documentation Tenant Isolation Known Issues